#Linux security
Explore tagged Tumblr posts
Text
Basic Linux Security (Updated 2025)
Install Unattended Upgrades and enable the "unattended-upgrades" service.
Install ClamAV and enable "clamav-freshclam" service.
Install and run Lynis to audit your OS.
Use the "last -20" command to see the last 20 users that have been on the system.
Install UFW and enable the service.
Check your repo sources (eg; /etc/apt/).
Check the /etc/passwd and /etc/shadow lists for any unusual accounts.
User the finger command to check on activity summaries.
Check /var/logs for unusual activity.
Use "ps -aux | grep TERM" or "ps -ef | grep TERM" to check for suspicious ongoing processes.
Check for failed sudo attempts with "grep "NOT in sudoers" /var/log/auth.log.
Check journalctl for system messages.
Check to make sure rsyslog is running with "sudo systemctl status rsyslog" (or "sudo service rsyslog status") and if it's not enable with "sudo systemctl enable rsyslog".
Perform an nmap scan on your machine/network.
Use netstat to check for unusual network activity.
Use various security apps to test you machine and network.
Change your config files for various services (ssh, apache2, etc) to non-standard configurations.
Disabled guest accounts.
Double up on ssh security by requiring both keys and passwords.
Check your package manager for any install suspicious apps (keyloggers, cleaners, etc).
Use Rootkit Scanners (chkrootkit, rkhunter).
Double SSH Security (Key + Password).
Disabled Guest Accounts.
Enabled Software Limiters (Fail2Ban, AppArmor).
Verify System Integrity via fsck.
Utilize ngrep/other networking apps to monitor traffic.
Utilize common honeypot software (endlessh).
Create new system-launch subroutines via crontab or shell scripts.
Ensure System Backups are Enabled (rsnapshot).
Check for suspicious kernel modules with "lsmod"
#linux#security#linuxsecurity#computersecurity#networking#networksecurity#opensource#open source#linux security#network#ubuntu#kali#parrot#debian#gentoo#redhat
175 notes
·
View notes
Text
Convert PuTTY PPK SSH keys to OpenSSH format for seamless use on Ubuntu systems. This step-by-step guide ensures your existing SSH keys work perfectly across different operating systems.
#Convert PPK Key for SSH#cross-platform SSH#key conversion#Linux security#OpenSSH#PPK format#PuTTY#SSH authentication#SSH client#SSH keys#Ubuntu
2 notes
·
View notes
Text
Guys, please make sure your Linux distro is updated: For Debian / Ubuntu distros run this command in a terminal:
sudo apt update && sudo apt upgrade
2 notes
·
View notes
Text
I think every computer user needs to read this because holy fucking shit this is fucking horrible.
So Windows has a new feature incoming called Recall where your computer will first, monitor everything you do with screenshots every couple of seconds and "process that" with an AI.
Hey, errrr, fuck no? This isn't merely because AI is really energy intensive to the point that it causes environmental damage. This is because it's basically surveilling what you are doing on your fucking desktop.
This AI is not going to be on your desktop, like all AI, it's going to be done on another server, "in the cloud" to be precise, so all those data and screenshot? They're going to go off to Microsoft. Microsoft are going to be monitoring what you do on your own computer.
Now of course Microsoft are going to be all "oooh, it's okay, we'll keep your data safe". They won't. Let me just remind you that evidence given over from Facebook has been used to prosecute a mother and daughter for an "illegal abortion", Microsoft will likely do the same.
And before someone goes "durrr, nuthin' to fear, nuthin to hide", let me remind you that you can be doing completely legal and righteous acts and still have the police on your arse. Are you an activist? Don't even need to be a hackivist, you can just be very vocal about something concerning and have the fucking police on your arse. They did this with environmental protesters in the UK. The culture war against transgender people looks likely to be heading in a direction wherein people looking for information on transgender people or help transitioning will be tracked down too. You have plenty to hide from the government, including your opinions and ideas.
Again, look into backing up your shit and switching to Linux Mint or Ubuntu to get away from Microsoft doing this shit.
44K notes
·
View notes
Text
I started to sour on MacOS about 20 years ago when I discovered that they had, without notice, substituted their own, nonstandard version of the readline library for the one that the rest of the unix-like world was using. This broke gnuplot¹ and a lot of other free software. The creator of curl², Daniel Stenberg, writes about how Apple is still breaking things, this time with serious security and privacy implications.
1 Anon ‘Gnuplot Homepage’. Available from: http://gnuplot.info/
2 Anon (n.d.) ‘Curl’. Available from: https://curl.se
0 notes
Text
I think it is very cool how tech companies, schools, employers, and universities make it actively difficult to distance yourself from Google, Microsoft, and Apple.
Yes most Linux distros are very stable, way more secure, privacy friendly, and way more customizable. But every institution is built to make technological independence as difficult as possible.
Yelling on the internet that everyone should switch to Linux and FOSS really ignores how much of the technological world is designed to not let that happen.
#yes switch to linux if you can#Data privacy and security needs to be addressed on a much larger legal scale#you cant consume your way out of this my friends#opensuse#linux#open source#data privacy
722 notes
·
View notes
Text
You either die a hero or you live long enough to see yourself become the villain ...

138 notes
·
View notes
Text
Masterpost of informational posts
All posts are written for everyone, including those with no prior computer science education. If you know how to write an email and have used a computer at least sparingly, you are qualified for understanding these posts. :)
What is a DDoS
What are the types of malware
Vulnerabilities and Exploits (old and somewhat outdated)
Example of how malware can enter your computer
What are botnets and sinkholes
How does passwords work
Guide for getting a safer password
Here are various malware-related posts you may find interesting:
Stuxnet
The North Korean bank heist
5 vintage famous malware
Trickbot the Trickster malware (old and not up to date)
jRAT the spy and controller (old and not up to date)
Evil malware
New to Linux? Here's a quick guide for using the terminal:
Part 1: Introduction
Part 2: Commands
Part 3: Flags
Part 4: Shortcuts
If you have any questions, request for a topic I should write about, or if there is something in these posts that you don't understand, please send me a message/ask and I'll try my best to help you. :)

- unichrome
Bonus: RGB terminal
#datatag#masterpost#malware#cybersecurity#infosec#security#hacking#linux#information#informative#computer science
424 notes
·
View notes
Text
If you're a linux[1] user who deploys multiple devices, I implore you: learn the command `scp`. It will change your life
It lets you copy files over an ssh pipe; if there's an ssh server on that host, you can essentially directly address a known file on that filesystem and say pwease gimme. And it's roughly the same syntax as `cp`, just with a `[user]@[host]:` before *either source or destination*[2].
And the real kicker is that neither source nor destination need be local:
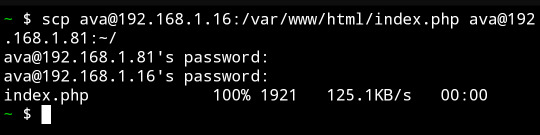
I copied a file from my web server to an icecast source client host by passing it through my phone.
Unreasonably handy tool to have on your toolbelt.
Footnotes under the cut.
[1] Okay, fine, you got me! It's not solely a linux util. SCP is part of the openssh suite, which means that it's available on virtually every OS under the sun... Including being included by default on Windows 10 1709 and later versions of Windows. It's already on your mac, your BSD system, and almost certainly your phone, too. SSH servers and *nix go together like picnics and baskets, though, so I wouldn't exactly pull the *average* windows user aside to recc' `scp`.
[2] What's most interesting to me is that the `[user]@[host]` is used for the SSH client to know where it's authenticating and how, but the actual filesystem location's format is not processed by the SSH client; it's the *server's* format, not the client, that matters for parsing the file location. In some cases this can lead to a mismatch on filenames that you're receiving vs requesting, but the -T flag disables that checking, and then use `[email protected]:D:\\Documents\\testdata.bin` (drive letter indicated and backslashes escaped) to refer to it
#openssh#scp#linux#i am sorry to secure contain protect fans who are uninterested in this being in your tags but. hash collisons happen
147 notes
·
View notes
Text
On Personal InfoSec
Been awhile since I've had one of these posts but I figure with all that's going on in the world it's time to make another one of these posts and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides.
Browsers:
There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out.
Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN:
Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Proton VPN: Has easily the most amount of countries serviced, can take cash payments, and does offer port forwarding.
Email Provider:
Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Outlook.com you'll need to pay.
Proton Mail: Secure, end-to-end encrypted, and fairly easy to setup and use. Offers a free option up to 1gb
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Email Client:
Thunderbird if you're on Windows or Linux
Apple Mail if you're on macOS
Cloud Storage:
Proton Drive: Encrypted cloud storage from the same people as Proton Mail.
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free, and open source.
Chat Clients:
Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode.
If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help.
I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#information security#infosec#computer security#computer infosec#personal infosec#browsers#internet browser#email#instant messaging#cloud storage#linux#pop os#linux mint#ubuntu#firefox#firefox extensions#long post
67 notes
·
View notes
Text
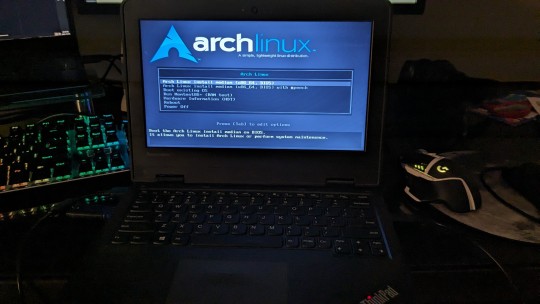
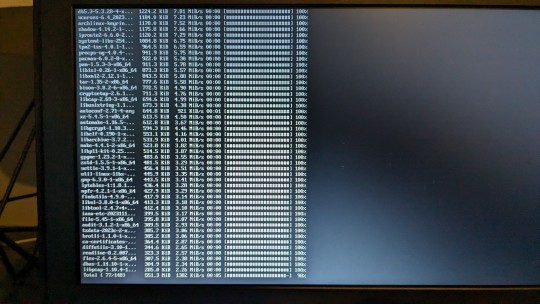
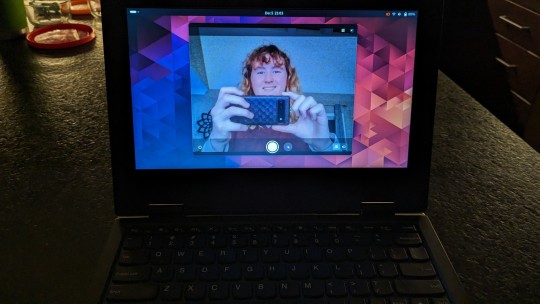
that time i, with zero prior linux experience, managed to install arch on an old-ass laptop and get the wifi to work :3
#linux#arch#I'd do it again on my main pc but I'm in uni so there's programs i need that flat-out won't work on linux#office shit and secure browsers for exams‚ and windows hello authentication#so sad.
59 notes
·
View notes
Text
one of the biggest advantages of customization in linux with keyboard only window managers is that you don't even need a good password. Typical windows users cannot use your computer, and for extra safety you can launch your window manager on all tty and remove the need for a password entirely (don't do that). You and only you know your custom system with absurd shortcuts to type to open anything at all that come from some obscure reference that not even your personal cia agent knows about.
#cool retro term#linux#linuxposting#sway#i3#other stuff#cyber security#trust me im a cyber security expert i promise look i just said it im a cyber security expert
52 notes
·
View notes
Text
Yuck. Zorin OS 17.3 switched its default browser to Brave. I kinda feel like I don’t trust the Zorin team anymore. Claiming to trust a Chromium Crypto Browser over Firefox (even if Mozilla did just pull some shady ass shit) makes me feel kinda anxious about trusting my data on their software. I wonder what other Linux distros run on modern MacBook hardware.
#rambles#linux#linuxposting#zorin#zorin os#firefox#mozilla#mozilla firefox#privacy#security#online privacy#online security#zorin is 17.3
15 notes
·
View notes
Text
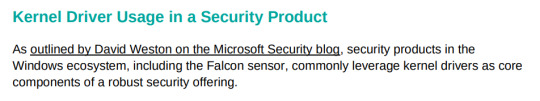
Crowdstrike directly calls out Microsoft in their latest incident report and its SO FUNNY. Its perfect condescending corpo speak and I love it.
People on Twitter: Why on earth does Crowdstrike need Windows kernel access ?!?!?!
Crowdstrike: because Windows sucks ass

#crowdstrike#fuck windows#cyber security#linux best os#most of the people complaining about this on twitter can't even tell you the difference between kernel space and userspace and it shows
46 notes
·
View notes
Text

Can't bots just trust we're human without the robot dance-off? 😄
#linux#linuxfan#linuxuser#ubuntu#debian#dev#devops#webdevelopment#programmingmemes#linuxmemes#memes#cat#coding#developer#tech#ethicalhacking#computerscience#coder#security#infosec#cyber
155 notes
·
View notes